Understanding the Basics of Crypto Tasks

Crypto tasks are an integral part of modern computing, ensuring the security and integrity of data. Whether you’re a developer, a system administrator, or simply someone interested in the field, understanding how to perform these tasks is crucial. In this article, we’ll delve into the various aspects of crypto tasks, providing you with a comprehensive guide to help you navigate this complex domain.
What are Crypto Tasks?
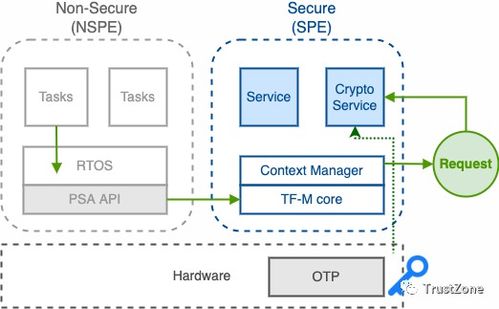
Crypto tasks refer to a range of operations that involve cryptographic algorithms and techniques. These tasks are designed to protect data from unauthorized access, ensure data integrity, and provide authentication. Common crypto tasks include encryption, decryption, hashing, digital signatures, and key management.
Encryption and Decryption
Encryption is the process of converting plaintext data into ciphertext, making it unreadable to anyone without the appropriate decryption key. Decryption, on the other hand, is the process of reversing this process, converting ciphertext back into plaintext. Here’s a brief overview of some popular encryption algorithms:
| Algorithm | Description |
|---|---|
| AES | Advanced Encryption Standard, a symmetric key encryption algorithm used widely in various applications. |
| RSA | Rivest-Shamir-Adleman, an asymmetric encryption algorithm that uses a public key for encryption and a private key for decryption. |
| DES | Data Encryption Standard, an older symmetric key encryption algorithm that has been largely replaced by AES. |
Hashing
Hashing is a process that converts data of any size into a fixed-size string of bytes. This string, known as a hash, is unique to the input data, making it useful for verifying data integrity and storing passwords securely. Some popular hashing algorithms include:
| Algorithm | Description |
|---|---|
| SHA-256 | Secure Hash Algorithm 256-bit, a cryptographic hash function designed by the National Security Agency (NSA). |
| MD5 | Message Digest Algorithm 5, a widely-used cryptographic hash function that produces a 128-bit hash value. |
| SHA-1 | Secure Hash Algorithm 1, a cryptographic hash function that produces a 160-bit hash value. |
Digital Signatures
Digital signatures are used to verify the authenticity and integrity of a message or document. They provide a way to ensure that the sender is who they claim to be and that the message has not been tampered with. Public-key cryptography, such as RSA, is commonly used to create digital signatures.
Key Management
Key management is a critical aspect of crypto tasks. It involves generating, storing, and distributing cryptographic keys securely. Proper key management is essential to ensure the security of encrypted data. Some key management best practices include:
- Use strong, random keys
- Store keys securely, using hardware security modules (HSMs) or other secure storage solutions
- Limit access to keys
- Regularly rotate keys
Tools and Libraries for Crypto Tasks
There are numerous tools and libraries available to help you perform crypto tasks. Some popular options include:
- Python’s `cryptography` library
- Node.js’s `crypto` module
- Rust’s `rustls` crate
- Dart’s `crypto` library
Conclusion
Crypto tasks are essential for protecting data in today’s digital world. By understanding the basics of encryption, decryption, hashing, digital signatures, and key management, you can ensure the security and integrity of your data. Utilize the available tools and libraries to perform these tasks efficiently and securely.


